In today's rapidly evolving digital world, security remains a top priority, especially for businesses handling sensitive information. One of the critical components of cybersecurity infrastructure is the Hardware Security Module (HSM), which plays a vital role in safeguarding data, encrypting sensitive communications, and maintaining the integrity of cryptographic keys.
What is a Hardware Security Module (HSM)?
A Hardware Security Module (HSM) is a physical device designed to manage and protect digital keys, perform encryption and decryption operations, and provide high-level security for cryptographic processes. HSMs are specialized hardware systems that are used to generate, store, and manage cryptographic keys securely. They are typically used in scenarios where sensitive data needs to be protected, such as in financial transactions, enterprise applications, government communications, and data storage.
The main advantage of using an HSM is that it provides an isolated, tamper-resistant environment for cryptographic operations, ensuring that sensitive information like private keys never leaves the secure environment of the module.
Types of HSMs
HSMs can be categorized into two main types:
- Network-Attached HSM: These modules are connected to a network and can be accessed remotely by various systems. They are commonly used in enterprise environments for centralized cryptographic operations.
- USB HSM: Smaller and portable, these modules are often used for individual or small-scale purposes. They connect via USB and are commonly used for secure authentication or digital signing.
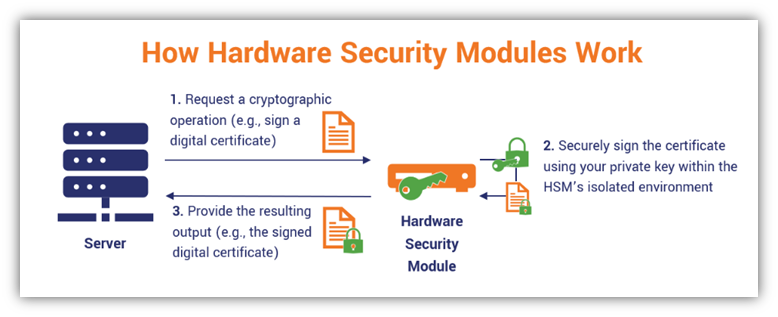
How Do HSMs Work?
HSMs work by creating a secure environment for cryptographic operations. When data needs to be encrypted or decrypted, the cryptographic keys are used inside the HSM to perform the operation. The keys never leave the HSM, which prevents them from being exposed to external threats.
Here’s an overview of how HSMs function:
- Key Generation: HSMs are capable of generating cryptographic keys, including symmetric keys, asymmetric key pairs, and digital certificates, all within a secure environment.
- Encryption and Decryption: When data is encrypted or decrypted, the HSM performs the operation using the cryptographic keys stored inside it, ensuring that these sensitive keys are never exposed to external systems.
- Key Management: HSMs provide capabilities to manage the lifecycle of cryptographic keys, such as key rotation, archiving, and secure deletion.
Applications of HSMs
Hardware Security Modules have a wide range of applications across various industries, including:
- Payment Processing: HSMs are critical for securing payment transactions. Banks, financial institutions, and credit card processors use HSMs to encrypt sensitive transaction data and protect payment card details.
- Digital Signatures: HSMs are used to generate digital signatures for software, contracts, and other documents, ensuring that the signer's identity is verified and the data has not been tampered with.
- Data Protection: In data centers and cloud environments, HSMs help secure sensitive data by encrypting it both at rest and in transit, protecting against unauthorized access.
- Government Applications: Many government agencies use HSMs for secure communications, protecting classified information, and ensuring data integrity in digital transactions.
- PKI Infrastructure: HSMs are an essential part of Public Key Infrastructure (PKI), which is used for secure communication, digital certificates, and encryption.
Benefits of Using an HSM
- Enhanced Security: HSMs provide strong, hardware-based encryption and key management, protecting against both physical and cyber threats.
- Tamper Resistance: The hardware design of HSMs makes them tamper-resistant, ensuring that even if the device is physically attacked, the sensitive data inside remains protected.
- Compliance: Many industries, such as finance, healthcare, and government, are required to comply with strict data protection regulations. HSMs help meet compliance standards like PCI-DSS, HIPAA, and GDPR.
- Performance: HSMs are optimized for high-performance cryptographic operations, ensuring that encryption and decryption processes are fast and efficient, even in high-volume environments.
- Key Lifecycle Management: HSMs offer secure key generation, storage, rotation, and destruction, ensuring the complete lifecycle of cryptographic keys is protected.
Challenges and Considerations
While HSMs offer high levels of security, there are some challenges and considerations to keep in mind:
- Cost: HSMs can be expensive, particularly the high-end models used in enterprise environments. However, their value in terms of security often justifies the cost.
- Complexity: Implementing and managing HSMs can be complex, especially in large-scale environments. It requires specialized knowledge and expertise to ensure proper integration.
- Performance: While HSMs are optimized for cryptographic operations, the added layer of hardware can sometimes cause latency in certain applications. Balancing security and performance is crucial.
Conclusion
In an era where cybersecurity threats are becoming increasingly sophisticated, the importance of protecting sensitive data cannot be overstated. Hardware Security Modules (HSMs) provide a robust solution for safeguarding cryptographic keys, securing sensitive communications, and ensuring compliance with regulatory standards. Whether in financial institutions, government organizations, or enterprise environments, HSMs play a crucial role in maintaining data integrity, confidentiality, and trust.